SMMA has designed highly secured spaces for the United States Air Force, the Navy, Army Reserve, and National Guard training facilities. The range of secured military spaces SMMA has designed includes arms vaults, communications security (COMSEC) areas, and secret internet protocol router network (SIPRNet) cafés, the latter presenting the most interesting design challenges.

Per the Army Reserve IT Manual, the implementation of a SIPRNet in an Army Reserve facility is based on data encryption within SIPRNet cafés. These spaces are dedicated to the transmission and reception of secure information. Strict adherence to United States Army Reserve Command (USARC) requirements must be maintained during the design and construction of such spaces.
What follows is an overview of the criteria used to design a SIPRNet café for a U.S. Army Reserve Command (USARC) facility.
This article is acronym heavy, and every effort has been made to spell out terms used by the Army Reserve.
The SIPRNet Café
Throughout the design process, the entire SIPRNet system is reviewed with, and approved by, a civilian division contracted by the USARC, known as the G6. The G6 manages the USARC Enterprise Architecture Program, directs a staff of Army civilians and contractors, and ensures that the activities of the USARC Enterprise Services Activity (ESA) Divisions (including Network Services, Network Applications, and Information Management Services) comply with USARC Enterprise Architecture.

Image: SCIF-in-a-Box by Trusted Systems. SCIF stands for Sensitive Compartmented Information Facility, a room or series of rooms that are designed to prevent unauthorized access to classified information.
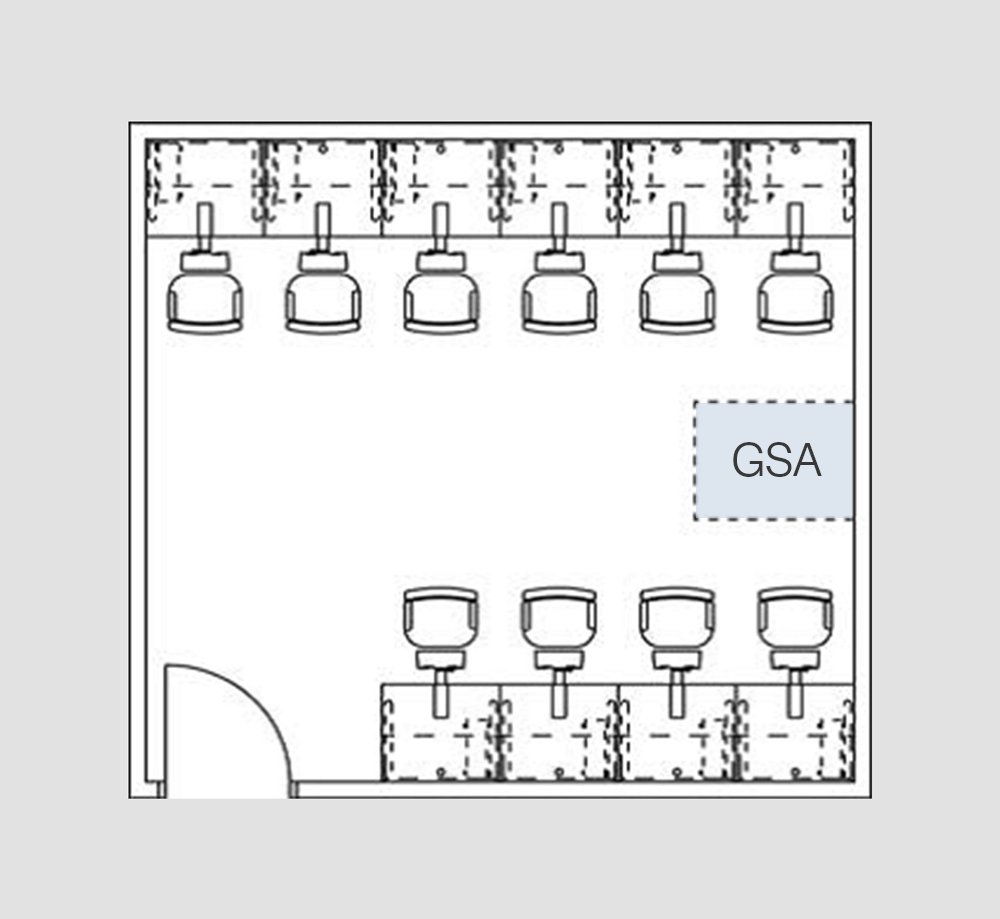
A standard SIPRNet café layout, taken from the Army Reserve IT Manual. Workstations are arranged around the perimeter of the room and a General Service Administration (GSA) network cabinet that houses secured network equipment used for encrypting and decrypting secret telecommunications.
SIPRNet Cable Color Coding
The SIPRNet telecommunications cable infrastructure is comprised of two assigned cable colors: black and red. These color designations are used to maintain physical separation of electrical and electronic circuits, components, equipment, and systems that handle national security information (RED), in electrical form, from those that handle non-national security information (BLACK) in the same form. The telecommunications subcontractor is responsible for providing the color-coded cable infrastructure to connect to the Government-provided equipment.
The BLACK System
The BLACK System, also known as the Sensitive but Unclassified (SBU) System, comprises standard telecommunications pathways, cables, devices, and equipment that are physically separated from the RED System. The BLACK System processes and carries only unclassified and/or encrypted information.
BLACK System communications lines, devices, and equipment must be installed at a minimum of 39 inches from the GSA-approved container, and a minimum of six inches from RED lines. BLACK voice and data outlets must be installed a minimum of 20 inches from RED outlets.
A two-inch intermediate or rigid steel conduit is provided from the GSA-approved container to the Telecommunications Equipment Room (TER), with BLACK backbone cables for the transmission of SBU communications.
The RED System
The RED System processes and carries unencrypted classified signals. It consists of telecommunications pathways, conduits, cables, devices, and equipment mounted on the walls for daily visual inspection, to allow detection of tampering. As noted above, the RED System is physically separated from the BLACK System. As its name indicates, cables and jacks are specified to be red.
The GSA-approved container is located to provide a minimum 39 inches of separation from BLACK lines, except the BLACK horizontal cables that connect to the GSA-approved container, noted above. It must also be located to provide a minimum of 39 inches of separation from fortuitous conductors, such as HVAC ducts, pipes, and equipment.
The protected distribution system constitutes a hardened distribution system that affords significant physical protection against unauthorized personnel from gaining access without being discovered.
RED cables are installed in electrical metallic tubing or steel conduit utilizing fittings of the same material. The conduit system is designed in a tree-type arrangement, beginning in the SIPRNet café with a single conduit sized to contain all the cables, while allowing for 50% growth. Pull boxes are used to branch the carrier cables to workstation outlets.

Intrusion-Detection System (IDS)
The SIPRNet café requires an IDS that consists of a balanced magnetic switch installed at the entrance door, complete motion detector coverage within the space, and an entry card reader. The Government provides the electronic devices, and the electronic security system subcontractor is responsible for conduit and back box provisions and power.
As an added security layer, a call button is at the entrance on the non-secured side of the door on the corridor wall adjacent to it. Personnel without the appropriate credentials who wish to enter the SIPRNet room use the call button to communicate with security personnel inside the space.
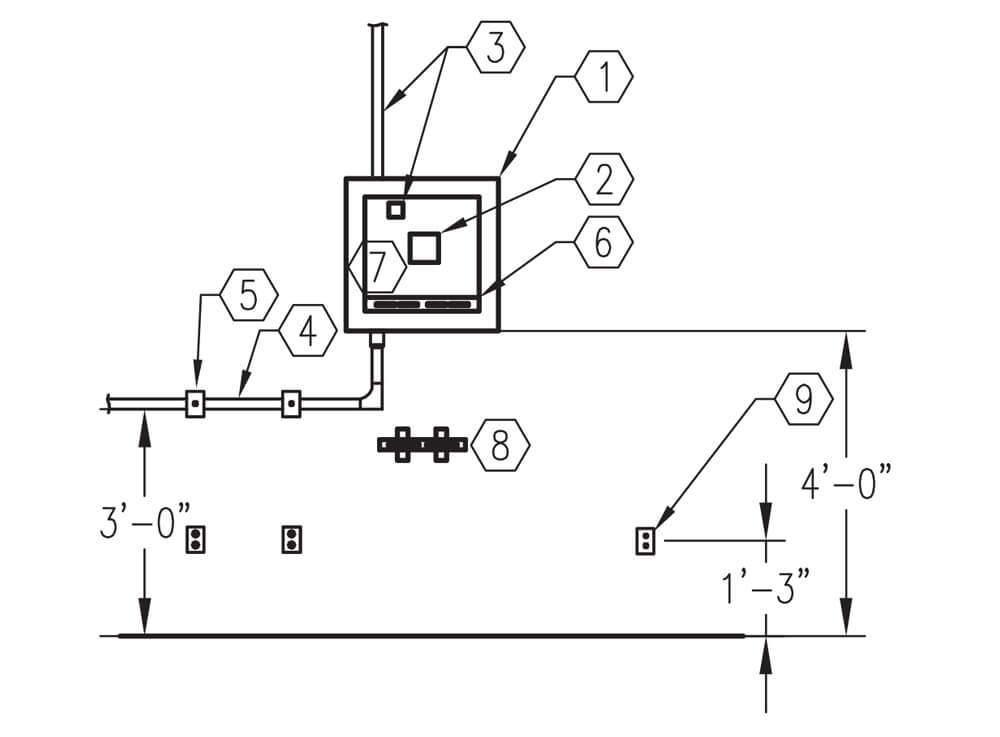
Elevation Diagram of a Typical SIPRNET Cafe Communications Equipment Cabinet Configuration
Additional Requirements
In addition to the telecommunication and security systems described above, the café must be designed and constructed to an extensive array of stringent building and mechanical system requirements, including:
These are constructed of plaster, gypsum, wallboard material, hardware, or other similar material that the command security manager deems to be of equal strength.
The access door to the room is substantially constructed of wood or metal. The hinge pins on out-swing doors are pinned, brazed, or spot-welded to prevent removal. The door is equipped with a built-in, GSA-approved combination lock meeting federal specifications.
Doors, other than the access door, are secured from the inside by a variety of means. Examples include deadbolt locks, panic deadbolt locks, and rigid wood and metal bars that extend across the width of the door. Key-operated locks that can be accessed from the exterior side of the door are prohibited.
Windows less than 18 feet above the ground when measured from the bottom of the window, or that are easily accessible by means of objects directly beneath the windows, are constructed from or covered with materials that provide protection from forced entry. This protection needs to be no stronger than the contiguous walls.
Utility openings, such as ducts and vents, are designed to be at less than a person-passable (96 square inches) opening. Openings larger than 96 square inches are hardened in accordance with Military Handbook 1013/1A, which provides guidance to ensure that appropriate physical security considerations are included in the design of facilities.
SMMA’s acquired expertise in the design of highly secure spaces like the SIPRNet café carries over in the design of other facilities that may not require the same level of protection, but demand the same level of detail to meet the specific criteria of a wide range of project types.
Perspective
Designing to Military Standards
Perspective






